Conducting due diligence on third parties is a critical step in managing vendor risks, compliance, and security. The Third-Party Risk Management (TPRM) module in GRCHub helps organizations evaluate vendor risks, monitor compliance, and identify vulnerabilities throughout the vendor lifecycle.
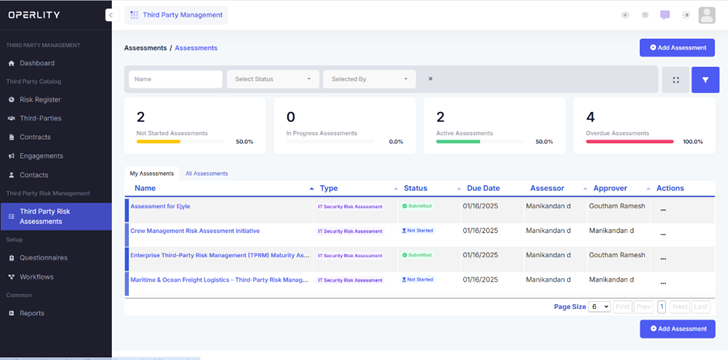
1. Continuous Monitoring of Third-Party Risk
Once a third party is onboarded and active, users should:
- Conduct periodic risk assessments to monitor vendor security.
- Use AI-powered tools to analyse vendor reports and identify vulnerabilities.
2. AI-Powered Document Processing
To automate risk identification, users can:
- Upload third-party documents such as:
- Vulnerability Assessment & Penetration Testing (VAPT) reports
- Security certificates
- Compliance audit reports
- The AI engine analyzes these documents and extracts potential security risks.
- Users can request the AI to automatically generate risks based on the identified vulnerabilities.
Example: If a VAPT report highlights critical security flaws, the AI will generate risks that require immediate action.
3. Why This Matters?
✅ Enhances efficiency and security in vendor risk management.
✅ Reduces manual effort in risk identification and assessment.
✅ Helps prioritize vendor risks and track remediation progress.
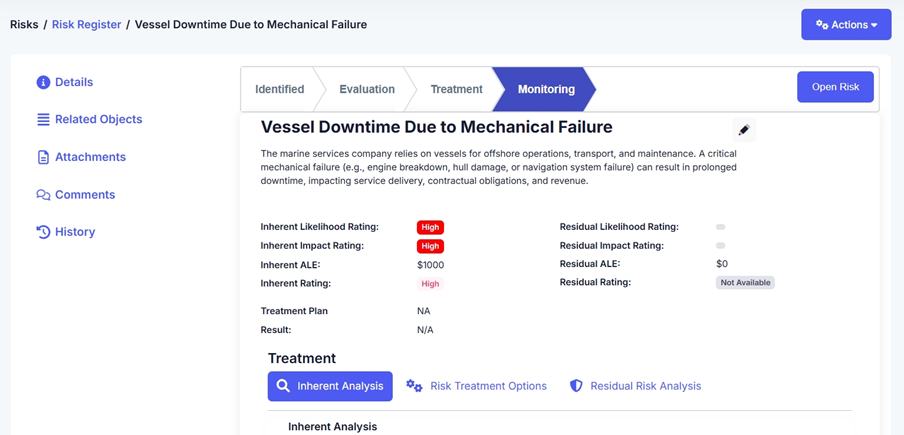
4. Managing the Risk Lifecycle
Once third-party risks are identified, users should follow the risk lifecycle:
- Risk Identification – Review the risks extracted by AI.
- Risk Assessment – Evaluate the severity and impact of the risks.
- Risk Mitigation – Assign corrective actions to the vendor.
- Ongoing Monitoring – Ensure continuous compliance through periodic audits.
Example: If a third party has a high-risk vulnerability, the organization can assign remediation actions and track the resolution progress.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article